SOC Home Lab Writeup
Defining the Problem Statement
This section grounds the project by discussing the necessity and context of the home lab build.
Building a Security Operations Centre (SoC) at home inherently presents challenges, particularly concerning limited resources, complexity, and integrating different tools. This project serves as a practical, cost-effective guide for setting up a modern SOC lab using entirely free and open-source technologies. For beginners, this lab is invaluable for gaining hands-on experience and showcasing knowledge. For seasoned professionals, it provides a crucial space to simulate and experiment with various security solutions before deploying them in production environments.
Technical Architecture
The technical overview details the setup using VirtualBox and outlines the role of each component.
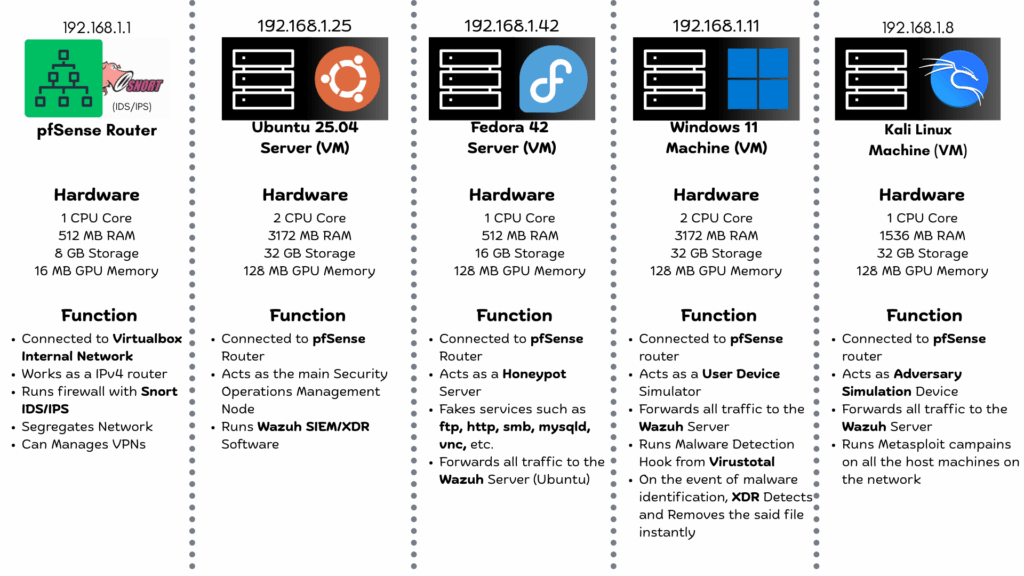
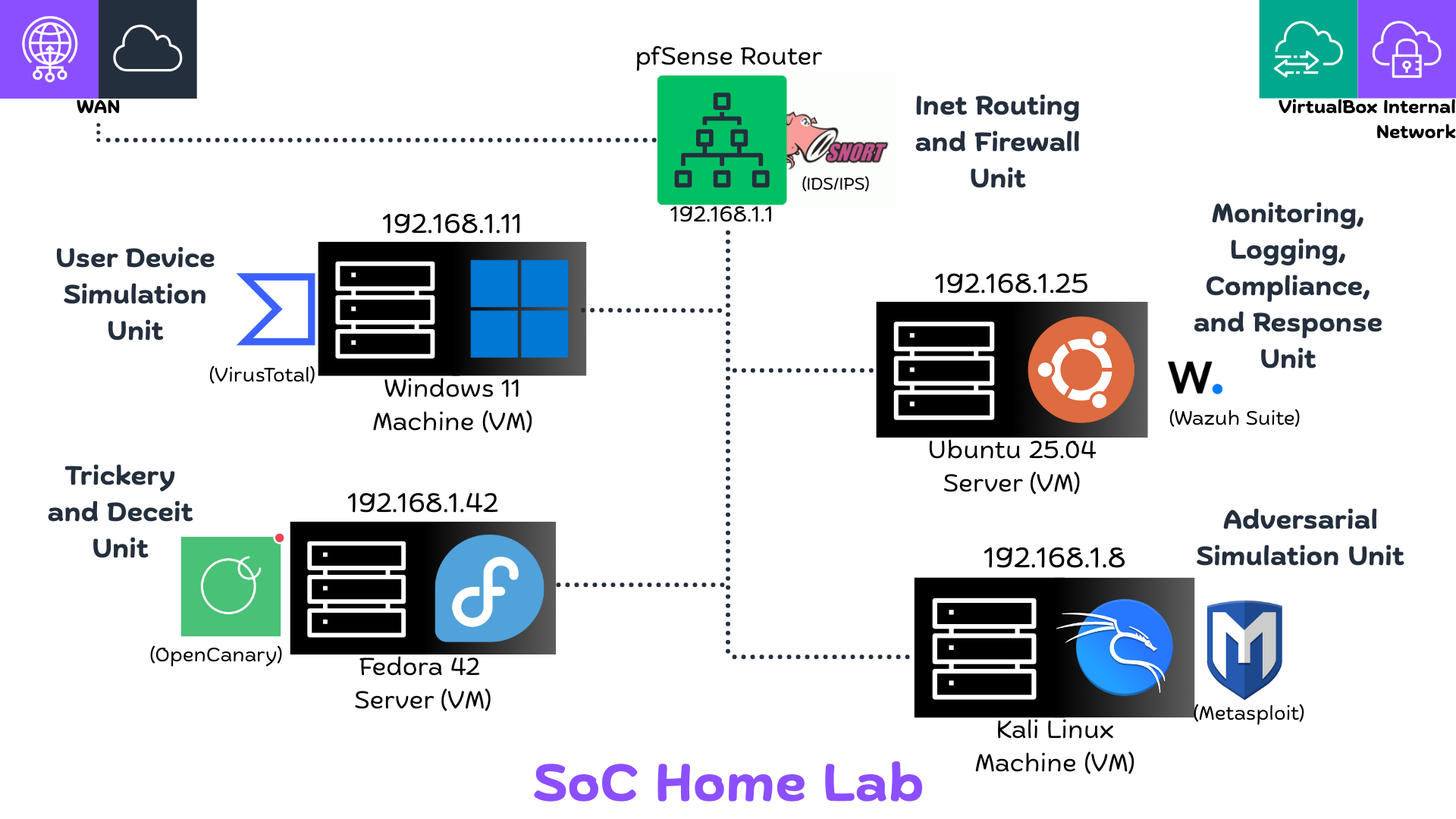
My home lab SOC setup leverages VirtualBox to host five distinct virtual machines (VMs), each assigned a specific role necessary for a functional security environment.
- pfSense Router (192.168.1.1): This machine acts as the network gateway. It routes traffic between the WAN port and the Internal network of VirtualBox. It also handles crucial security functions, running a firewall and IDS/IPS via Snort, and can be used to manage VPNs or create a DMZ to segregate the internal network.
- Ubuntu Server (192.168.1.25): This is the heart of the SOC, running Wazuh SIEM/XDR. It serves as the main machine managing security operations.
- Fedora Server (192.168.1.42): This functions as the Honeypot server. It is responsible for faking various services and forwarding any suspicious traffic or interactions directly to the Wazuh server.
- Windows 11 Machine (192.168.1.11): This simulates a standard user device. It runs malware detection and forwards its event logs to the SIEM.
- Kali Linux Machine (192.168.1.8): This is the Adversary simulation device. It is used for running attack campaigns and testing the effectiveness of the deployed detection capabilities.
Key Features and Capabilities
This section focuses on the specific security benefits and tools implemented in the lab.
The integration of open-source tools provides several robust security capabilities:
- Intelligent XDR: Using Wazuh to automatically detect malware and, critically, trigger an instant response to remove it. This acts like having a personal digital security guard.
- Next-Gen Networking: pfSense brings enterprise-grade firewalling and routing to the home network, offering a significant learning experience.
- Web Security Monitoring: Wazuh is configured to flag attacks such as SQL injection and arbitrary input attacks against web applications in real-time.
- Robust Honeypot: OpenCanary is implemented to simulate vulnerable services. It serves as a trap to attract and analyze attacks up close. When OpenCanary detects interaction with fake services, it alerts the Wazuh Server, which can then be hooked into systems like mail or Discord.
- Adversarial Campaigns: Metasploit scripts to generate realistic attack traffic, running automated scripts to perform Adversarial Campaigns and test the deployed defenses.
The Setup: From Prerequisite to Configuration
This section provides a summary of the practical steps involved, noting that detailed instructions are available elsewhere (e.g., GitHub).
Building this lab requires specific resources and involves a multi-step installation and configuration process.
Hardware Requirements: To run every component smoothly, a robust computer is necessary, ideally featuring an Intel i5 10th Gen / AMD Ryzen 5 3600 processor, 8 logical processors, 16 GB DDR4 memory (with at least 8 GB free), and at least 128 GB of free storage space.
Installation Overview: The process begins with installing Oracle VirtualBox and acquiring the necessary guest OS image files (ISOs) for pfSense, Ubuntu Server, Windows 11, Fedora Server, and Kali Linux. Key installation steps include:
- Setting up pfSense with two network adapters (Bridged for WAN, Internal Network for LAN).
- Setting up the Windows 11 VM (including optional steps like disabling Windows Defender for testing).
- Setting up the Kali Linux VM and updating packages.
- Setting up the Fedora Server.
- Installing the Wazuh manager on the Ubuntu Server, which provides access credentials upon successful installation.
Configuration Highlights: After installation, the focus shifts to configuration:
- Accessing the Wazuh Dashboard via HTTPS and using the provided credentials.
- Adding the Windows, Kali, and Fedora VMs as Wazuh Agents.
- Configuring the Windows Machine for Malware Removal XDR using Wazuh and Virustotal, and setting up SMB discoverability for testing.
- Setting up OpenCanary on the Fedora Server and correctly forwarding its logs to Wazuh.
- Configuring Snort Firewall on the pfSense Router.
Learning Outcomes: Skills Gained
This section summarizes the knowledge and hands-on experience acquired through the project.
By the end of this lab, you are able to:
- Understand the architecture and components of a modern Security Operations Center (SoC).
- Configure and manage a virtualized network environment using pfSense.
- Deploy and manage Wazuh as a SIEM/XDR solution.
- Implement a honeypot using OpenCanary to detect and analyze malicious activity.
- Gain hands-on experience with malware detection and incident response.
- Simulate adversary attacks using Kali Linux and analyze the effectiveness of security controls.
- Learn how to integrate different security tools and technologies for comprehensive threat detection and prevention.
Looking Ahead: Future Enhancements
The conclusion looks forward to potential additions, emphasizing the modular design of the lab.
This project was designed with flexibility in mind, ensuring future seamless integration. Potential enhancements I plan to explore include:
- OpenCTI Integration: Incorporating OpenCTI to enhance threat intelligence capabilities.
- DMZ Zones: Creating dedicated DMZ zones for user and adversary simulation to improve network segmentation and security.
- Additional Security Tools: Incorporating tools like Sysmon and Suricata to further enhance monitoring and detection.
- Active Directory: Implementing Active Directory to simulate a more realistic enterprise environment.
- Android Machine Integration: Incorporating an Android virtual machine for mobile application security testing.